GCC 14 -fanalyzer improvements for buffer overflows and more -- David Malcolm
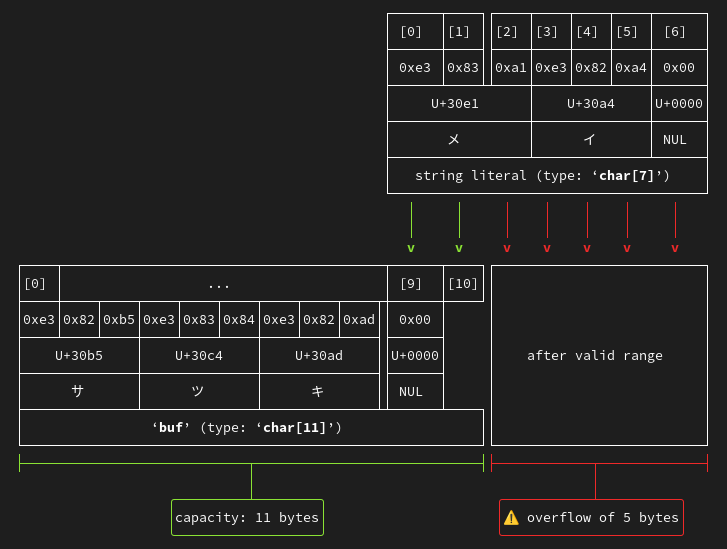 For anyone interested in the top source of memory safety issues, out-of-bounds accesses... GCC 14 will be able to catch more cases, and even show them with some colorful retro ASCII art:
For anyone interested in the top source of memory safety issues, out-of-bounds accesses... GCC 14 will be able to catch more cases, and even show them with some colorful retro ASCII art:
Improvements to static analysis in the GCC 14 compiler
by David Malcolm
It does require some source code annotation, but also delivers safety value in return.
From the article:
So for GCC 14, I've added the ability for the analyzer to emit text-based diagrams visualizing the spatial relationships in a predicted buffer overflow. ... [For example,] this diagram shows the destination buffer populated by the content from thestrcpycall, and thus the existing terminatingNULbyte used for the start of thestrcatcall. For non-ASCII strings ... it can show the UTF-8 representation of the characters ...... [Another improvement] is that the analyzer now simulates APIs that scan a buffer expecting a null terminator byte, and will complain about code paths where a pointer to a buffer that isn't properly terminated is passed to such an API.
Plus more, such as:
The analyzer has a form of "taint analysis", which tracks attacker-controlled inputs, places where they are sanitized, and places where they are used without sanitization. In previous GCC releases this was too buggy to enable by default, with lots of false positives, so I hid it behind an extra command-line argument. I've fixed many bugs with this, so for GCC 14 I've enabled this by default when -fanalyzer is selected. This also enables these 6 taint-based warnings:

 If you are a C++ developer who uses VS Code as your editor, Copilot Chat can help you with many of your everyday coding tasks by allowing you to iterate with your code in natural language.
If you are a C++ developer who uses VS Code as your editor, Copilot Chat can help you with many of your everyday coding tasks by allowing you to iterate with your code in natural language. A new episode of the series about SObjectizer and message passing:
A new episode of the series about SObjectizer and message passing:
 A new episode of the series about SObjectizer and message passing:
A new episode of the series about SObjectizer and message passing: I delivered a keynote, C++ and the Next 30 Years, at the 2024 CPP-Summit conference in Beijing, China. Experiencing the culture, the people, and the landscape was tremendous. In this post I’ll cover some of the points in my future-looking C++ talk and share my experience giving a talk for the first time in China.
I delivered a keynote, C++ and the Next 30 Years, at the 2024 CPP-Summit conference in Beijing, China. Experiencing the culture, the people, and the landscape was tremendous. In this post I’ll cover some of the points in my future-looking C++ talk and share my experience giving a talk for the first time in China. In C++, shadowing occurs when a name in one scope hides an identical name in another scope, sparking debate over its merit. This article explores scenarios where shadowing can either protect code integrity or hinder its evolution, highlighting its dual nature and impact on code maintenance. Join Raymond as he unravels the complexities of shadowing in C++, revealing its intricate balance between benefit and drawback.
In C++, shadowing occurs when a name in one scope hides an identical name in another scope, sparking debate over its merit. This article explores scenarios where shadowing can either protect code integrity or hinder its evolution, highlighting its dual nature and impact on code maintenance. Join Raymond as he unravels the complexities of shadowing in C++, revealing its intricate balance between benefit and drawback. A new episode of the series about SObjectizer and message passing:
A new episode of the series about SObjectizer and message passing: