C++26: Erroneous Behaviour -- Sandor Dargo

[[indeterminate]] attribute for cases where deliberate uninitialized values are needed.
C++26: Erroneous Behaviour
by Sandor Dargo
From the article:
If you pick a random talk at a C++ conference these days, there is a fair chance that the speaker will mention safety at least a couple of times. It’s probably fine like that. The committee and the community must think about improving both the safety situation and the reputation of C++.
If you follow what’s going on in this space, you are probably aware that people have different perspectives on safety. I think almost everybody finds it important, but they would solve the problem in their own way.
A big source of issues is certain manifestations of undefined behaviour. It affects both the safety and the stability of software. I remember that a few years ago when I was working on some services which had to support a 10x growth, one of the important points was to eliminate undefined behaviour as much as possible. One main point for us was to remove uninitialized variables which often lead to crashing services.
Thanks to P2795R5 by Thomas Köppe, uninitialized reads won’t be undefined behaviour anymore - starting from C++26. Instead, they will get a new behaviour called “erroneous behaviour”.
The great advantage of erroneous behaviour is that it will work just by recompiling existing code. It will diagnose where you forgot to initialize variables. You don’t have to systematically go through your code and let’s say declare everything as
autoto make sure that every variable has an initialized value. Which you probably wouldn’t do anyway.But what is this new behaviour that on C++ Reference is even listed on the page of undefined behaviour? It’s well-defined, yet incorrect behaviour that compilers are recommended to diagnose. Is recommended enough?! Well, with the growing focus on safety, you can rest assured that an implementation that wouldn’t diagnose erroneous behaviour would be soon out of the game.

 Contract assertions, introduced in proposal P2900 for C++26, provide a robust mechanism for runtime correctness checks, offering more flexibility and power than the traditional
Contract assertions, introduced in proposal P2900 for C++26, provide a robust mechanism for runtime correctness checks, offering more flexibility and power than the traditional  When working with a mutex-protected variable, you often need to read or modify its value while holding the lock, but then operate on the value outside the lock to minimize contention. While the traditional approach involves copying the value within a locked scope, using an immediately-invoked lambda or helper function can streamline this process, enabling efficient copy elision or move semantics to optimize performance.
When working with a mutex-protected variable, you often need to read or modify its value while holding the lock, but then operate on the value outside the lock to minimize contention. While the traditional approach involves copying the value within a locked scope, using an immediately-invoked lambda or helper function can streamline this process, enabling efficient copy elision or move semantics to optimize performance. In this blog post, we’ll explore implementing order-independent keyword arguments for C++ through use of C++26’s
In this blog post, we’ll explore implementing order-independent keyword arguments for C++ through use of C++26’s 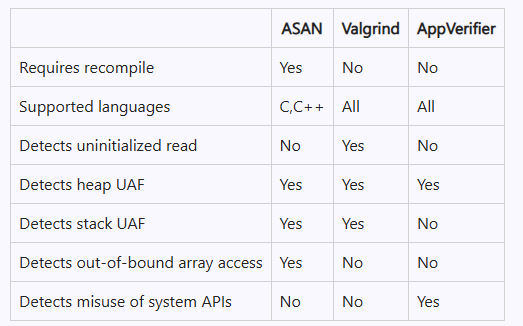
 Bjarne Stroustrup, the creator of C++, has outlined his vision for the language’s future in his article "21st Century C++," emphasizing the need for safer and more modern coding practices without abandoning its powerful legacy. His approach advocates for incremental improvements, such as guideline-enforcing profiles and enhanced type safety, ensuring C++ remains relevant in an era of heightened security and performance demands.
Bjarne Stroustrup, the creator of C++, has outlined his vision for the language’s future in his article "21st Century C++," emphasizing the need for safer and more modern coding practices without abandoning its powerful legacy. His approach advocates for incremental improvements, such as guideline-enforcing profiles and enhanced type safety, ensuring C++ remains relevant in an era of heightened security and performance demands.