A brief introduction to C++ structured binding--Raymond Chen
Did you know about it?
A brief introduction to C++ structured binding
by Raymond Chen
From the article:
C++17 introduced a feature known as structured binding. It allows a single source object to be taken apart...

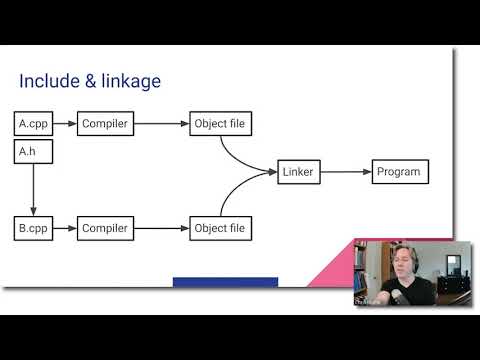 The basics.
The basics.