 The safety of C++ has become a hot topic recently. Herb Sutter discusses the language’s current problems and potential solutions.
The safety of C++ has become a hot topic recently. Herb Sutter discusses the language’s current problems and potential solutions.
Overload 180: C++ Safety, In Context
by Herb Sutter
From the article:
We must make our software infrastructure more secure against the rise in cyberattacks (such as on power grids, hospitals, and banks), and safer against accidental failures with the increased use of software in life-critical systems (such as autonomous vehicles and autonomous weapons).
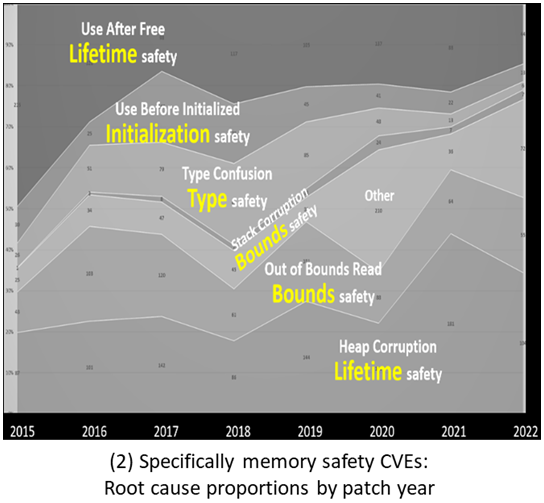
The past two years in particular have seen extra attention on programming language safety as a way to help build more-secure and -safe software; on the real benefits of memory-safe languages (MSLs); and that C and C++ language safety needs to improve – I agree.
But there have been misconceptions, too, including focusing too narrowly on programming language safety as our industry’s primary security and safety problem – it isn’t. Many of the most damaging recent security breaches happened to code written in MSLs (e.g., Log4j [CISA-1]) or had nothing to do with programming languages (e.g., Kubernetes Secrets stored on public GitHub repos [Kadkoda23]).
In that context, I’ll focus on C++ and try to:
- highlight what needs attention (what C++’s problem is), and how we can get there by building on solutions already underway;
- address some common misconceptions (what C++’s problem isn’t), including practical considerations of MSLs; and
- leave a call to action for programmers using all languages.
tl;dr: I don’t want C++ to limit what I can express efficiently. I just want C++ to let me enforce our already-well-known safety rules and best practices by default, and make me opt out explicitly if that’s what I want. Then I can still use fully modern C++… just nicer.
Let’s dig in.

Add a Comment
Comments are closed.