Talk: Who’s Afraid of the Big Bad Template -- Coral Kashri
Templates and metaprogramming considered as the big bad wolf of C++, and it’s time to stop being scared of this wolf, as it’s one of the most powerful creatures of C++.
Talk: Who’s Afraid of the Big Bad Template
by Coral Kashri
From the description:
In this talk I’ve demonstrated the power of this incredible creature, while I hope that this talk would be an easy enterence to this concept (pan intended), and to help you developing the anticipation to walk into the cave of metaprogramming.
The talk was give on Core C++ 2025.

 Conferences are never just about the talks — they’re about time, travel, tradeoffs, and the people you meet along the way. After a year of attending several C++ events across formats and cities, this post is a personal look at how different conferences balance technical depth, community, and the experience of being there.
Conferences are never just about the talks — they’re about time, travel, tradeoffs, and the people you meet along the way. After a year of attending several C++ events across formats and cities, this post is a personal look at how different conferences balance technical depth, community, and the experience of being there.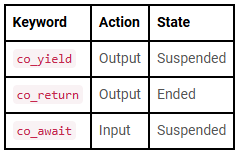 C++20 introduced coroutines. Quasar Chunawala, our guest editor for this edition, gives an overview.
C++20 introduced coroutines. Quasar Chunawala, our guest editor for this edition, gives an overview. Filtering items from a container is a common situation. Bartłomiej Filipek demonstrates various approaches from different versions of C++.
Filtering items from a container is a common situation. Bartłomiej Filipek demonstrates various approaches from different versions of C++. std::chrono::high_resolution_clock sounds like the obvious choice when you care about precision, but its name hides some important caveats. In this article, we’ll demystify what “high resolution” really means in <chrono>, why this clock is often just an alias, and when—if ever—it’s actually the right tool to use.
std::chrono::high_resolution_clock sounds like the obvious choice when you care about precision, but its name hides some important caveats. In this article, we’ll demystify what “high resolution” really means in <chrono>, why this clock is often just an alias, and when—if ever—it’s actually the right tool to use.