Constructing Containers from Ranges in C++23 -- Sandor Dargo

std::from_range tag, a range and an optional allocator. These from_range constructors make it easier to construct containers from ranges, helping make C++ code more concise, more expressive, and less error-prone.
Constructing Containers from Ranges in C++23
by Sandor Dargo
From the article:
I’ve written plenty on this blog about standard algorithms, but far less about ranges. That’s mostly because, although I’ve had production-ready compilers with C++20 ranges since late 2021, the original ranges library lacked a few key capabilities.
The biggest gap was at the end of a pipeline: you could transform data lazily, but you couldn’t drop the result straight into a brand-new container. What you got back was a view; turning that view into, say, a
std::vectorstill required the old iterator-pair constructor.C++23 fixes that in two complementary ways:
std::to(an adaptor that finishes a pipeline by converting to a container), andfrom_rangeconstructors on every standard container.Today we’ll focus on the second improvement, because it’s the one you can implement in your own types, too.
The
from_rangeconstructorEvery standard container now supports a new set of constructors that make integration with ranges smoother — the so-called
from_rangeconstructors.These constructors allow you to build a container directly from a range, rather than from a pair of iterators.

 Time flies—C++ Insights just turned 7! To celebrate, I’ve upgraded the tool to Clang 20, unlocking even more C++23 and C++26 features for you to explore.
Time flies—C++ Insights just turned 7! To celebrate, I’ve upgraded the tool to Clang 20, unlocking even more C++23 and C++26 features for you to explore. Visual Studio 2022 version 17.14 is now generally available! This post summarizes the new features you can find in this release for C++. You can download Visual Studio 2022 from the
Visual Studio 2022 version 17.14 is now generally available! This post summarizes the new features you can find in this release for C++. You can download Visual Studio 2022 from the  C++’s undefined behaviour impacts safety. Sandor Dargo explains how and why uninitialised reads will become erroneous behaviour in C++26, rather than being undefined behaviour.
C++’s undefined behaviour impacts safety. Sandor Dargo explains how and why uninitialised reads will become erroneous behaviour in C++26, rather than being undefined behaviour. Registration is now open for CppCon 2025! The conference starts on September 15 and will be held
Registration is now open for CppCon 2025! The conference starts on September 15 and will be held 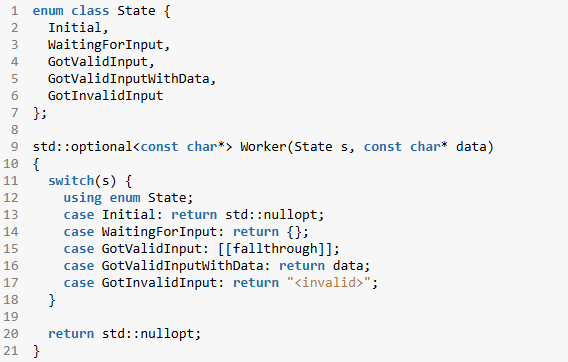
 Registration is now open for CppCon 2025! The conference starts on September 15 and will be held
Registration is now open for CppCon 2025! The conference starts on September 15 and will be held